Short on time?
This is the best antivirus for Mac:
Norton– Perfect antivirus protection for Mac and a ton of bonus features: A free and unlimited VPN, a password manager, and a firewall.
Your Mac is not immune to threats — yet. Our free Mac antivirus protects on 3 fronts. Malware isn't the only threat to your Mac. Malicious websites and vulnerable Wi-Fi.
Do you need to buy antivirus software for your Mac? It's a question we frequently get. The answer is simple: Yes, you do. There are two main reasons. The first is the rise of malware specifically designed for macOS. The second is that the best security software for Mac do far more than protect you frommalware.
- Download latest antivirus and internet security solution for Mac OS. Protect your Mac with precise and powerful virus protection now. Try now for free.
- Intego — Best Overall Mac Antivirus of 2020. Specifically designed for Macs, Intego has a wide.
By including features such as a firewall, parental controls, a password manager, and a virtual private network (VPN), they protect not only your MacBook, but also your privacy, passwords and family. But buyer beware: Many antivirus for Mac are watered-down versions of their siblings for Windows, lacking many of the essential security features.
So how to find the best antivirus for your Mac? We are here to help. Since 2014, we have tested and reviewed 100's of antivirus for Mac, Windows, Android and iOS.
The best antivirus for Mac are:
Norton
The best antivirus for Mac. Antivirus, firewall, VPN and a password manager.
- Malware Protection100%100%
- Online Privacy100%100%
✓ Windows, Mac, Android, and iOS
✓ 60-days money-back guarantee
✓ VPN: Free and unlimited
Intego
Excellent protection. Antivirus, firewall, parental controls and an optional VPN.
- Malware Protection100%100%
- Online Privacy98%98%
✓ 30-days money-back guarantee
✓ VPN: Not included for free
- Malware Protection100%100%
- Online Privacy72%72%
✓ 30-days money-back guarantee
✓ VPN: 200 mb per day for free
- Malware Protection100%100%
- Online Privacy70%70%
✓ 30-days money-back guarantee
✓ VPN: 200 mb per day for free
- Malware Protection100%100%
- Online Privacy56%56%
✓ Mac only
✓ 30-days money-back guarantee
✓ VPN: Not included
The full reviews
Below you can read more in our reviews of the best 5 antivirus of 2020
Norton Review
Verdict: Perfect protection, and the best privacy features
Pros:
- Perfect anti-malware for Mac: Norton detected and eliminated 100% of the malware samples in the tests.
- Anti-phishing: Norton's anti-phishing technology warns you when you are about to visit a dangerous website.
- Password protection: Norton helps you create and store highly secure passwords.
- Smart firewall: Norton's firewall keeps suspicious devices from connecting to your Mac. Protecting your from snooping eyes.
- Free and unlimited VPN: With Norton's VPN you can encrypt your internet connecting. Allowing you to be completely anonymous online.
Cons:
- No parental controls: It's too bad that Norton's Parental Controls are only available to Windows users. Parents can consider buying Intego instead.
For more information, read Norton's full review.
Navigate this page
Intego Review
Verdict: Perfect protection, and the best parental controls
Pros:
- Perfect anti-malware for Mac: Intego found and removed all malware samples in the tests.
- Firewall: Intego's two-way firewall blocks untrusted devices from connecting to your Mac, and prevents malicious apps on your device from sending information to their developers.
- Parental controls: Intego is one of the few to offer parental controls on Mac. Its ContentBarrier allows you to censor the internet for your kids.
Cons:
- No anti-phishing: Intego does not warn you when visiting suspicious websites, known to trick people into handing over sensitive information.
- No password manager: Intego does not help you to create and store highly secure passwords.
- No free VPN: Without a VPN you can't encrypt your internet connection and be anonymous online. A paid VPN is available at extra cost.
Adobe photoshop cs6 for mac os x 10.13. For more information, read Intego's full review.
BitDefender Review
Verdict: Perfect anti-malware, but missing several features
Pros:
- Perfect anti-malware for Mac: Just like the others, BitDefender discovered and deleted all malware samples in the tests.
- Anti-phishing: BitDefender's anti-phishing tools warn you about websites that try to trick you in handing over sensitive data.
- Anti-tracker: BitDefender's anti-tracker browser extension keeps ads from following you around the web, by blocking tracking cookies.
- Free VPN for 200 MB per day: Encrypt your internet connection with BitDefender's VPN. Making you anonymous and untraceable online.
Cons:
- No password manager: BitDefender's password manager is for Windows only. So it won't help you create, store and manage passwords.
- No firewall: Because BitDefender has no firewall, devices can simply connect to you Mac whenever they please.
- VPN limited to 200 MB per day: 200 MB is very little online. And if you want the unlimited VPN, you'll need to pay extra.
- No parental controls: To access BitDefender's parental controls, you'll need to upgrade to its Total Security package, which is more expensive.
For more information, read BitDefender's full review.
Kaspersky Review
Verdict: Perfect protection, but some features are limited
Pros:
- Perfect anti-malware for Mac: Kaspersky removed 100% of the malware samples in the tests.
- Basic password protection: Kaspersky includes a free (but limited) password manager, helping you to create and store secure passwords.
- Basic firewall: Kaspersky's firewall isn't a complete version like Norton's, but it does monitor your Mac's ports and is able to block attacks.
- Free VPN for 200 MB per day: Kaspersky's VPN allows you to surf the web in anonymity and safe from hackers (but only for 200 MB per day).
- Basic parental controls: Kaspersky includes a basic version of its Safe Kids feature, allowing you to restrict what your children can view online.
Cons:
- Limited password protection: Kaspersky's full multi-device password manager, as available in its Total Security package, costs extra.
- VPN limited to 200 MB per day: 200 MB per day isn't a lot when browsing the web. To access the limitless VPN, you'll need to pay extra.
- Limited parental controls: To track your children's location, monitor their social media, and access other premium features, you'll need to pay extra.
For more information, read Kaspersky's full review.
Airo AV Review
Verdict: Perfect anti-malware, but not much else
Pros:
- Perfect anti-malware for Mac: Airo detected and removed 100% of the malware samples in the test.
- Anti-phishing: Airo's anti-phishing browser extension warns you before you visit malicious websites that try to steal you personal information.
- Lightweight antivirus: Airo does not have many additional features. This does, however, make it very lightweight and require few resources.
Cons:
- No password manager: Airo doesn't help you create and store highly secure passwords like Norton.
- No firewall: Without a Firewall, Airo cannot keep unwanted devices from connecting to your Mac without permission.
- No VPN: With Airo, you can't encrypt your internet connection to become anonymous online and safe from hackers.
- No parental controls: Airo AV doesn't offer you the ability to view and censor what your children do online.
For more information, read Airo's full review.
MacOS is far safer than Windows and Android. This is in part because there are fewer malware that target Apple's operating software. And in part, because macOS has several anti-malware features built-in:
GateKeeper sends a warning signal when apps that lack a digital signature are executed. XProtect compares files with known malware samples. And the Malware Removal Tool does what its name suggest; remove malware.
Yet security experts generally agree that adding an additional layer of protection on top of Apple's built-in defences is a wise decision for 3 reasons:
- Apple's security measures function well against known-malware, but are too slow to respond to newly emerging threats.
- Apple isn't immune to making mistakes. AV-Comparatives, one of the two leading antivirus testing labs, found a security flaw in macOS Mojave 10.14.4 as recently as March 2019.
- Today's threats revolve around more than just malware. In our connected world, anti-phishing and privacy features are just as important as anti-malware.
So in our quest for the best antivirus software for macOS, we test for 3 things: Protection, privacy and speed.
As all 3 factors matters, but not in the same proportion, we have assigned a different weight factor to each:
- Protection50%50%
- Privacy30%30%
- Speed20%20%
Protection
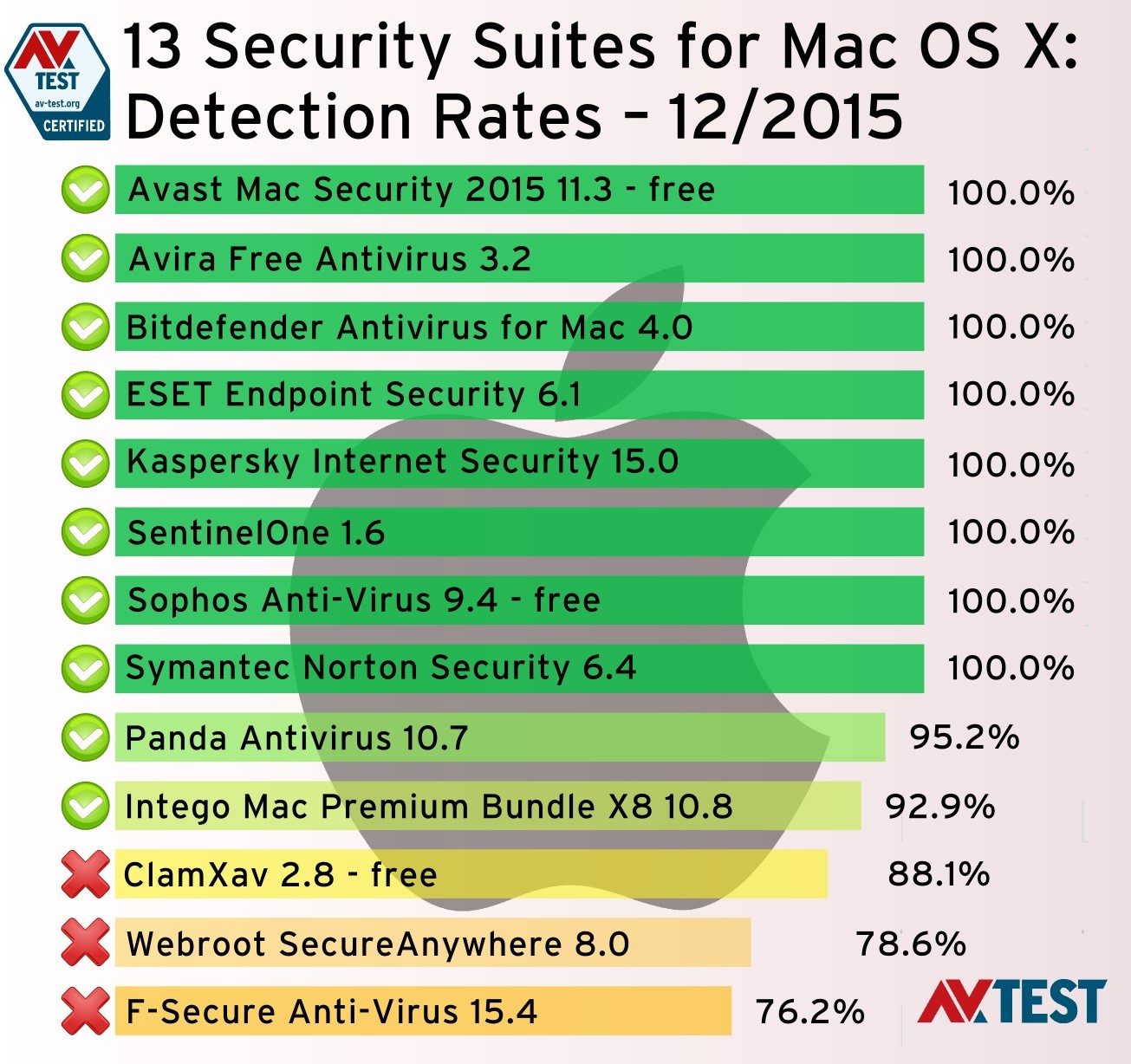
Both AV-Test and AV-Comparatives, the leading antivirus testing labs, carry out large scale anti-malware tests for macOS at least once a year. Their findings form the basis of our analysis in the protection category.
In their Malware Protection Tests, as they are aptly called, an antivirus software is installed on a freshly updated MacBook, after which it is exposed to just under 600 malware samples.
These samples range from the very harmful to the fairly harmless, such as adware that hitch a ride with bundled software. The samples also include close cousins: Malware samples that are similar, but modified enough to avoid detection from XProtect's blacklist of known malware.
Although the malware sample count of only 600 is very small in comparison to the 10.000+ malware samples used for Windows, it is an accurate representation of the malware for macOS out there in the 'wild'.
The low number of malware samples is the reason why all 5 of the antivirus for Mac on our list have a 100% detection rate. In such a limited malware library, any antivirus that doesn't score at least a 99% protection rate, is considered a failure.
The testing process itself is fairly straightforward. After the macOS systems have been (re-)installed, updated and equipped with the latest antivirus software, a USB drive containing the malware samples is introduced.
There are now 3 moments at which the antivirus software can intervene:
- Antivirus can notice some or all threats once the USB is inserted.
- If available, a USB scan is executed, during which the antivirus has another chance of detecting the malware samples.
- If any samples are left undetected and/or undeleted, these are moved to the Mac's hard disk and executed. Allowing the antivirus software a final attempt at quarantining and deleting the threats.
We use these findings by the testing labs, to reach our protection score.
Privacy
The data industry continues to expand. Governments, Internet Service Providers (ISPs), advertisers, and tech firms are all attempting to track your every move online.
In a time where even a big antivirus brand was caught selling its user's data (Yes Avast, we're talking about you), consumers are right to worry.
Luckily, the desire to be anonymous online has sparked fresh innovation. New cybersecurity firms have sprouted left and right, and created several technological solutions to help you protect you privacy.
By far the most important of these is the Virtual Private Network (VPN). A relatively straightforward yet ingenious solution that allows you to encrypt your internet connection, and in turn become fully anonymous online.
It works as follows: Instead of surfing the web directly, you establish an encrypted connection to a VPN server first. Then you continue surfing the web as you normally would.
Now anyone attempting to trace your online behaviour back to you, is actually tracing your behaviour back of that server, which is used by thousands of people. It's like attempting to discover your home address, but only finding a busy train station. Voila, you are anonymous.
At SoftwareLab, we test the VPN of each of the security companies, and check several factors:
- How does the VPN connection influence your upload and download speed, and your latency (ping)?
- How many servers are available and in what regions?
- What security features does the VPN have (AES-256 encryption, a kill-switch and the OpenVPN protocol are key features)?
- How much does the VPN cost?
- Who owns the VPN? Has the antivirus company created its own VPN (as Norton has), bought an existing VPN firm (as McAfee has), or is it selling a partner's VPN service under its own name (as BitDefender, Panda, and BullGuard do)?

The final privacy score is largely dependent on the quality of the VPN. But it is still influenced by the presence (or lack thereof) of other privacy features, such as a webcam and microphone protection, and an anti-tracker.
Speed
The final factor that we take into consideration when selecting the best antivirus for macOS, is the impact on the operating speed.
All software that operate continuously in the background require a certain amount of resources to run. But it shouldn't be noticeable.
AV-Test dedicates a specific part of their test to measuring the impact a security tool has on the operating speed – called the performance section. We use their test results, combined with our own experience working with the antivirus software, to reach an objective verdict in this category.
What is Adware?
Adware is freely distributed software that contains and displays built-in advertisements for various products and services. It is also a type of software that can redirect queries to various sponsor websites. Another facet of adware software is data collection, which is usually done for marketing purposes.
This type of software, depending on how complex it is, can collect search history results, keystrokes, keywords, search patterns, and sometimes even personal information, most often without the user's consent. Adware doesn't always have to be installed manually. It can be installed remotely on a user's computer when they visit an infected website. Hackers can also install malicious adware via a backdoor.
What is Antivirus?
Antiviruses are among the most important lines of defense of computers and other internet-enabled devices. Antivirus programs or program suites are designed to detect threats, quarantine them, remove them, as well as prevent them from accessing the target computer or network in the first place.
RealPlayer for Mac is the perfect desktop client to manage all your photos and videos, both local and in the cloud, all in one place. Keep your smartphones, tablets and HDDs lean without losing your moment. If you record countless GBs at a concert, just upload the clips to RealCloud using RealTimes and access them anywhere. RealPlayer for Mac 2020 full offline installer setup for Mac RealTimes (with RealPlayer) for Mac enables you to move, watch and share your videos. When you share videos with friends and family they'll be able to play them on any device or operating system, without downloading the app. Mac os for real player.
Depending on the complexity of the antivirus software, it can protect against low-key and high-risk attacks and invasions of privacy such as those made possible by hacking, viruses, worms, adware, rootkits, spyware, keyloggers, and others. While sandbox detection techniques are the most popular, various detection algorithms are implemented today, the most modern of which use data mining and machine learning.
What is a Botnet?
A botnet is a network of hijacked internet-connected devices that can be used for their superior combined computing power to deliver powerful attacks, disrupt internet traffic, or send spam. In a botnet, the hijacked computers are infected with bots, software programs that can perform automated tasks. Each computer in the network can operate one or more bots.
Also known as a zombie army or a zombie network, a botnet can be used by its owner through C&C software. Some threat actors may choose to use botnets for their own DDoS attacks, while others may rent out the botnet to interested third parties with malicious intent of their own.
What is a Computer Exploit?
Various command sequences, as well as pieces of software, code, and data may fall under the category of computer exploits when they are used to exploit certain software or hardware vulnerabilities on foreign devices or networks. Depending on the vulnerability, a computer exploit can be assigned to a specific subtype, all contingent on what the exploit can do to a foreign system thanks to the vulnerability it takes advantage of.
Exploits can be local and remote. Remote vulnerabilities allow varying degrees of access remotely while local vulnerabilities usually imply than an exploit cannot be used unless the origin of the attack comes from within the vulnerable device or network. This too can sometimes be accessed remotely if there is backdoor access into the system.
What is a Computer Virus?
A computer virus is usually a self-replicating malicious code that can copy itself into new programs, documents, or boot sectors, thus altering the way in which a device works. Computer viruses can be spread knowingly or unknowingly, but they need to be activated on the target device to have any effect. That's why many viruses are embedded into software that looks trustworthy and legitimate or hidden inside links to websites that are seemingly legit.
There is also a risk of transmission through infected storage devices such as USB drives. Viruses can target system memory or core functions of apps and hardware components. Transmission mac not downloading. They can also be designed to copy or delete data, or even encrypt it, which is something that's often used in ransomware.
What is a Computer Worm?
A computer worm is a subclass of computer viruses that rarely requires any help from the user (i.e. opening a program) to self-replicate and propagate itself in a vast network of interconnected devices. Worms usually get into a system either by direct download or through an unprotected network connection. Once inside a system, a worm can replicate itself multiple times and spread to other devices.
Although worms are sometimes viewed as a less threatening subclass, they are also often used to install backdoors into systems. These backdoors can then be used to install other malicious malware like keyloggers, adware, spyware, or bots, as well as to lay the foundation for a DDoS attack.
What is Computer Hacking?
Computer hacking, or just hacking, is any unauthorized intrusion into a computer or computer network. Such actions usually involve compromising the system security by either altering some of its features or bypassing security measures altogether to achieve anything from access to confidential information to establishing root access to that system.
The term hacking doesn't always imply negative activities. While there are people who use their skills to hack into foreign systems for personal, financial, or political gain, there are also those who hack into systems only to test their security and discover flaws or exploits. As a result of this type of hacking, many vulnerabilities can be patched before malicious hackers can exploit them.
What is Cybercrime?
For a crime to qualify as a cybercrime, it needs to either target a computer or use a computer as a tool to commit the offense. Although there are various subtypes of cybercrime, they can all be categorized into two larger types – crimes that target individual computers or networks and those that target the device owners.
Some of the most common types of cybercrime include bank information theft, identity theft, cyberterrorism, online predatory crimes, and online stalking. Not all cybercrimes are end-game actions. Some of them are simply one small step in a much larger scheme that extends to the offline world as well.
What is a DDoS Attack?
A DDoS attack is most often carried out by a botnet or zombie army of computers. It stands for distributed denial-of-service attack. The terminology refers to the disruption of services – either of a network or, say, a website. This is achieved by flooding target devices with unwanted internet traffic that hampers their performance.
The most common targets for DDoS attacks are online vendors, marketplaces, as well as other businesses that depend on having a stable connection and cannot afford to lose bandwidth. DDoS attacks may not only slow the performance of the targeted system but can also corrupt data or lead to data loss, not to mention significant financial losses.
What is Identity Theft?
Identity theft is used to describe any unauthorized gathering of personal identifying information, achieved by any means, physically or in the virtual world. Identity theft can be done via shoulder-surfing, stealing bank statements, obtaining fingerprints, dumpster diving, and so many more methods. The perpetrator uses this information to assume the victim's identity and gain personal benefit.
In this day and age, identity theft is more often than not classified as a cybercrime due to the fact that it involves hacking computer networks and databases for private information. It can also be done via spyware, keyloggers, planting viruses, email phishing, and other types of actions classified as cybercrimes.
What is a Keylogger?
There are two types of keyloggers. There are hardware keyloggers and software keyloggers. Regardless of which one is used, the main goal is always the same: tracking someone's keystrokes in order to monitor and record whatever it is they're doing on a device, whether they're browsing the internet, writing emails, writing code, etc.
Keyloggers are not always used with malicious intent. They can be used in cognitive writing research, to monitor employees on their work computers, or monitor underage kids and their online activities. However, they tend to have a negative connotation since they're most often used as standalone tools or part of advanced rootkits to steal confidential information or grant access to target devices.
What is Malware?
The term malware (short for malicious software) denotes all harmful pieces software such as computer viruses and worms, Trojans, ransomware, and adware, among others. Cybercriminals use it to establish a backdoor into foreign systems, create botnets, and launch various attacks for the purpose of stealing, corrupting, or deleting data on the target systems.
A malware suite, or a collection of more than one types of malicious software, is often referred to as a rootkit. Multiple types of covert malware programs can be embedded in a single application or file.
What is Phishing?
Phishing is a fraudulent act that involves the theft of credit card numbers, usernames, passwords, and other sensitive information in which a criminal poses as a trustworthy individual or business. Over the internet, phishing usually involves the use of fake websites with seemingly trustworthy domain names.
Although quite dangerous, phishing is usually easily avoidable if the user exercises more caution when opening attachments, disclosing their personal information, checking website URLs, and using up-to-date antivirus software. Phishing can't be successful without some involuntary help from the victims themselves, hence the need for cybercriminals to impersonate legitimate entities when phishing for information.

What is Ransomware?
Ransomware is a type of malware that is most often associated with holding certain files, data, or financial assets hostage. This malware can be remotely installed via a backdoor or downloaded by the user from infected websites or attachments. Once inside the target's system, the malware encrypts information that cannot be decrypted without a key. Other designations for ransomware include crypto-Trojan, crypto-worm, or crypto-virus.
Ransomware is also sometimes used to steal information. As a result, it is used in online blackmailing schemes in which the victim is threatened with the release of potentially compromising personal information that's been encrypted by the hacker unless a ransom is paid off. Finding the source of the attack or the attacker is generally very difficult since most ransoms involve cryptocurrency payouts.
What is a Rootkit?
Rootkits are usually, but not always, malware suites comprised of multiple programs and viruses designed to grant access to a computer or computer network by secretly exploiting various system vulnerabilities. Rootkits can be distributed via attachments, adware, email links, and other means.
The most common goal for a rootkit is establishing a backdoor access to the target system, which will allow the attacker to easily steal information, documents, money, or passwords. The perpetrator can also use this to wreak havoc on the system by corrupting data, disrupting traffic, deleting data, or slowing down the system's performance. Modern antivirus programs have rootkit detection, whereas this was a much more difficult problem to deal with in the past.
What is a Scam?
Best Antivirus For Mac Os X El Capitan
A scam is a fraudulent and criminal action initiated by an individual or group of individuals for the purpose of extracting sensitive information, stealing money, repurposing goods, etc. Internet scams include fake donations, cold calls, chain mail, online surveys, and many more.
A large majority of scams are done via the internet due to the ease of access that scammers have to networks of people. Some scams are quick schemes with a well-defined goal while others are larger cons that involve multiple steps in establishing trust, obtaining sensitive information, and stealing money.
What is Social Engineering?

The best antivirus for Mac. Antivirus, firewall, VPN and a password manager.
- Malware Protection100%100%
- Online Privacy100%100%
✓ Windows, Mac, Android, and iOS
✓ 60-days money-back guarantee
✓ VPN: Free and unlimited
Intego
Excellent protection. Antivirus, firewall, parental controls and an optional VPN.
- Malware Protection100%100%
- Online Privacy98%98%
✓ 30-days money-back guarantee
✓ VPN: Not included for free
- Malware Protection100%100%
- Online Privacy72%72%
✓ 30-days money-back guarantee
✓ VPN: 200 mb per day for free
- Malware Protection100%100%
- Online Privacy70%70%
✓ 30-days money-back guarantee
✓ VPN: 200 mb per day for free
- Malware Protection100%100%
- Online Privacy56%56%
✓ Mac only
✓ 30-days money-back guarantee
✓ VPN: Not included
The full reviews
Below you can read more in our reviews of the best 5 antivirus of 2020
Norton Review
Verdict: Perfect protection, and the best privacy features
Pros:
- Perfect anti-malware for Mac: Norton detected and eliminated 100% of the malware samples in the tests.
- Anti-phishing: Norton's anti-phishing technology warns you when you are about to visit a dangerous website.
- Password protection: Norton helps you create and store highly secure passwords.
- Smart firewall: Norton's firewall keeps suspicious devices from connecting to your Mac. Protecting your from snooping eyes.
- Free and unlimited VPN: With Norton's VPN you can encrypt your internet connecting. Allowing you to be completely anonymous online.
Cons:
- No parental controls: It's too bad that Norton's Parental Controls are only available to Windows users. Parents can consider buying Intego instead.
For more information, read Norton's full review.
Navigate this page
Intego Review
Verdict: Perfect protection, and the best parental controls
Pros:
- Perfect anti-malware for Mac: Intego found and removed all malware samples in the tests.
- Firewall: Intego's two-way firewall blocks untrusted devices from connecting to your Mac, and prevents malicious apps on your device from sending information to their developers.
- Parental controls: Intego is one of the few to offer parental controls on Mac. Its ContentBarrier allows you to censor the internet for your kids.
Cons:
- No anti-phishing: Intego does not warn you when visiting suspicious websites, known to trick people into handing over sensitive information.
- No password manager: Intego does not help you to create and store highly secure passwords.
- No free VPN: Without a VPN you can't encrypt your internet connection and be anonymous online. A paid VPN is available at extra cost.
Adobe photoshop cs6 for mac os x 10.13. For more information, read Intego's full review.
BitDefender Review
Verdict: Perfect anti-malware, but missing several features
Pros:
- Perfect anti-malware for Mac: Just like the others, BitDefender discovered and deleted all malware samples in the tests.
- Anti-phishing: BitDefender's anti-phishing tools warn you about websites that try to trick you in handing over sensitive data.
- Anti-tracker: BitDefender's anti-tracker browser extension keeps ads from following you around the web, by blocking tracking cookies.
- Free VPN for 200 MB per day: Encrypt your internet connection with BitDefender's VPN. Making you anonymous and untraceable online.
Cons:
- No password manager: BitDefender's password manager is for Windows only. So it won't help you create, store and manage passwords.
- No firewall: Because BitDefender has no firewall, devices can simply connect to you Mac whenever they please.
- VPN limited to 200 MB per day: 200 MB is very little online. And if you want the unlimited VPN, you'll need to pay extra.
- No parental controls: To access BitDefender's parental controls, you'll need to upgrade to its Total Security package, which is more expensive.
For more information, read BitDefender's full review.
Kaspersky Review
Verdict: Perfect protection, but some features are limited
Pros:
- Perfect anti-malware for Mac: Kaspersky removed 100% of the malware samples in the tests.
- Basic password protection: Kaspersky includes a free (but limited) password manager, helping you to create and store secure passwords.
- Basic firewall: Kaspersky's firewall isn't a complete version like Norton's, but it does monitor your Mac's ports and is able to block attacks.
- Free VPN for 200 MB per day: Kaspersky's VPN allows you to surf the web in anonymity and safe from hackers (but only for 200 MB per day).
- Basic parental controls: Kaspersky includes a basic version of its Safe Kids feature, allowing you to restrict what your children can view online.
Cons:
- Limited password protection: Kaspersky's full multi-device password manager, as available in its Total Security package, costs extra.
- VPN limited to 200 MB per day: 200 MB per day isn't a lot when browsing the web. To access the limitless VPN, you'll need to pay extra.
- Limited parental controls: To track your children's location, monitor their social media, and access other premium features, you'll need to pay extra.
For more information, read Kaspersky's full review.
Airo AV Review
Verdict: Perfect anti-malware, but not much else
Pros:
- Perfect anti-malware for Mac: Airo detected and removed 100% of the malware samples in the test.
- Anti-phishing: Airo's anti-phishing browser extension warns you before you visit malicious websites that try to steal you personal information.
- Lightweight antivirus: Airo does not have many additional features. This does, however, make it very lightweight and require few resources.
Cons:
- No password manager: Airo doesn't help you create and store highly secure passwords like Norton.
- No firewall: Without a Firewall, Airo cannot keep unwanted devices from connecting to your Mac without permission.
- No VPN: With Airo, you can't encrypt your internet connection to become anonymous online and safe from hackers.
- No parental controls: Airo AV doesn't offer you the ability to view and censor what your children do online.
For more information, read Airo's full review.
MacOS is far safer than Windows and Android. This is in part because there are fewer malware that target Apple's operating software. And in part, because macOS has several anti-malware features built-in:
GateKeeper sends a warning signal when apps that lack a digital signature are executed. XProtect compares files with known malware samples. And the Malware Removal Tool does what its name suggest; remove malware.
Yet security experts generally agree that adding an additional layer of protection on top of Apple's built-in defences is a wise decision for 3 reasons:
- Apple's security measures function well against known-malware, but are too slow to respond to newly emerging threats.
- Apple isn't immune to making mistakes. AV-Comparatives, one of the two leading antivirus testing labs, found a security flaw in macOS Mojave 10.14.4 as recently as March 2019.
- Today's threats revolve around more than just malware. In our connected world, anti-phishing and privacy features are just as important as anti-malware.
So in our quest for the best antivirus software for macOS, we test for 3 things: Protection, privacy and speed.
As all 3 factors matters, but not in the same proportion, we have assigned a different weight factor to each:
- Protection50%50%
- Privacy30%30%
- Speed20%20%
Protection
Both AV-Test and AV-Comparatives, the leading antivirus testing labs, carry out large scale anti-malware tests for macOS at least once a year. Their findings form the basis of our analysis in the protection category.
In their Malware Protection Tests, as they are aptly called, an antivirus software is installed on a freshly updated MacBook, after which it is exposed to just under 600 malware samples.
These samples range from the very harmful to the fairly harmless, such as adware that hitch a ride with bundled software. The samples also include close cousins: Malware samples that are similar, but modified enough to avoid detection from XProtect's blacklist of known malware.
Although the malware sample count of only 600 is very small in comparison to the 10.000+ malware samples used for Windows, it is an accurate representation of the malware for macOS out there in the 'wild'.
The low number of malware samples is the reason why all 5 of the antivirus for Mac on our list have a 100% detection rate. In such a limited malware library, any antivirus that doesn't score at least a 99% protection rate, is considered a failure.
The testing process itself is fairly straightforward. After the macOS systems have been (re-)installed, updated and equipped with the latest antivirus software, a USB drive containing the malware samples is introduced.
There are now 3 moments at which the antivirus software can intervene:
- Antivirus can notice some or all threats once the USB is inserted.
- If available, a USB scan is executed, during which the antivirus has another chance of detecting the malware samples.
- If any samples are left undetected and/or undeleted, these are moved to the Mac's hard disk and executed. Allowing the antivirus software a final attempt at quarantining and deleting the threats.
We use these findings by the testing labs, to reach our protection score.
Privacy
The data industry continues to expand. Governments, Internet Service Providers (ISPs), advertisers, and tech firms are all attempting to track your every move online.
In a time where even a big antivirus brand was caught selling its user's data (Yes Avast, we're talking about you), consumers are right to worry.
Luckily, the desire to be anonymous online has sparked fresh innovation. New cybersecurity firms have sprouted left and right, and created several technological solutions to help you protect you privacy.
By far the most important of these is the Virtual Private Network (VPN). A relatively straightforward yet ingenious solution that allows you to encrypt your internet connection, and in turn become fully anonymous online.
It works as follows: Instead of surfing the web directly, you establish an encrypted connection to a VPN server first. Then you continue surfing the web as you normally would.
Now anyone attempting to trace your online behaviour back to you, is actually tracing your behaviour back of that server, which is used by thousands of people. It's like attempting to discover your home address, but only finding a busy train station. Voila, you are anonymous.
At SoftwareLab, we test the VPN of each of the security companies, and check several factors:
- How does the VPN connection influence your upload and download speed, and your latency (ping)?
- How many servers are available and in what regions?
- What security features does the VPN have (AES-256 encryption, a kill-switch and the OpenVPN protocol are key features)?
- How much does the VPN cost?
- Who owns the VPN? Has the antivirus company created its own VPN (as Norton has), bought an existing VPN firm (as McAfee has), or is it selling a partner's VPN service under its own name (as BitDefender, Panda, and BullGuard do)?
The final privacy score is largely dependent on the quality of the VPN. But it is still influenced by the presence (or lack thereof) of other privacy features, such as a webcam and microphone protection, and an anti-tracker.
Speed
The final factor that we take into consideration when selecting the best antivirus for macOS, is the impact on the operating speed.
All software that operate continuously in the background require a certain amount of resources to run. But it shouldn't be noticeable.
AV-Test dedicates a specific part of their test to measuring the impact a security tool has on the operating speed – called the performance section. We use their test results, combined with our own experience working with the antivirus software, to reach an objective verdict in this category.
What is Adware?
Adware is freely distributed software that contains and displays built-in advertisements for various products and services. It is also a type of software that can redirect queries to various sponsor websites. Another facet of adware software is data collection, which is usually done for marketing purposes.
This type of software, depending on how complex it is, can collect search history results, keystrokes, keywords, search patterns, and sometimes even personal information, most often without the user's consent. Adware doesn't always have to be installed manually. It can be installed remotely on a user's computer when they visit an infected website. Hackers can also install malicious adware via a backdoor.
What is Antivirus?
Antiviruses are among the most important lines of defense of computers and other internet-enabled devices. Antivirus programs or program suites are designed to detect threats, quarantine them, remove them, as well as prevent them from accessing the target computer or network in the first place.
RealPlayer for Mac is the perfect desktop client to manage all your photos and videos, both local and in the cloud, all in one place. Keep your smartphones, tablets and HDDs lean without losing your moment. If you record countless GBs at a concert, just upload the clips to RealCloud using RealTimes and access them anywhere. RealPlayer for Mac 2020 full offline installer setup for Mac RealTimes (with RealPlayer) for Mac enables you to move, watch and share your videos. When you share videos with friends and family they'll be able to play them on any device or operating system, without downloading the app. Mac os for real player.
Depending on the complexity of the antivirus software, it can protect against low-key and high-risk attacks and invasions of privacy such as those made possible by hacking, viruses, worms, adware, rootkits, spyware, keyloggers, and others. While sandbox detection techniques are the most popular, various detection algorithms are implemented today, the most modern of which use data mining and machine learning.
What is a Botnet?
A botnet is a network of hijacked internet-connected devices that can be used for their superior combined computing power to deliver powerful attacks, disrupt internet traffic, or send spam. In a botnet, the hijacked computers are infected with bots, software programs that can perform automated tasks. Each computer in the network can operate one or more bots.
Also known as a zombie army or a zombie network, a botnet can be used by its owner through C&C software. Some threat actors may choose to use botnets for their own DDoS attacks, while others may rent out the botnet to interested third parties with malicious intent of their own.
What is a Computer Exploit?
Various command sequences, as well as pieces of software, code, and data may fall under the category of computer exploits when they are used to exploit certain software or hardware vulnerabilities on foreign devices or networks. Depending on the vulnerability, a computer exploit can be assigned to a specific subtype, all contingent on what the exploit can do to a foreign system thanks to the vulnerability it takes advantage of.
Exploits can be local and remote. Remote vulnerabilities allow varying degrees of access remotely while local vulnerabilities usually imply than an exploit cannot be used unless the origin of the attack comes from within the vulnerable device or network. This too can sometimes be accessed remotely if there is backdoor access into the system.
What is a Computer Virus?
A computer virus is usually a self-replicating malicious code that can copy itself into new programs, documents, or boot sectors, thus altering the way in which a device works. Computer viruses can be spread knowingly or unknowingly, but they need to be activated on the target device to have any effect. That's why many viruses are embedded into software that looks trustworthy and legitimate or hidden inside links to websites that are seemingly legit.
There is also a risk of transmission through infected storage devices such as USB drives. Viruses can target system memory or core functions of apps and hardware components. Transmission mac not downloading. They can also be designed to copy or delete data, or even encrypt it, which is something that's often used in ransomware.
What is a Computer Worm?
A computer worm is a subclass of computer viruses that rarely requires any help from the user (i.e. opening a program) to self-replicate and propagate itself in a vast network of interconnected devices. Worms usually get into a system either by direct download or through an unprotected network connection. Once inside a system, a worm can replicate itself multiple times and spread to other devices.
Although worms are sometimes viewed as a less threatening subclass, they are also often used to install backdoors into systems. These backdoors can then be used to install other malicious malware like keyloggers, adware, spyware, or bots, as well as to lay the foundation for a DDoS attack.
What is Computer Hacking?
Computer hacking, or just hacking, is any unauthorized intrusion into a computer or computer network. Such actions usually involve compromising the system security by either altering some of its features or bypassing security measures altogether to achieve anything from access to confidential information to establishing root access to that system.
The term hacking doesn't always imply negative activities. While there are people who use their skills to hack into foreign systems for personal, financial, or political gain, there are also those who hack into systems only to test their security and discover flaws or exploits. As a result of this type of hacking, many vulnerabilities can be patched before malicious hackers can exploit them.
What is Cybercrime?
For a crime to qualify as a cybercrime, it needs to either target a computer or use a computer as a tool to commit the offense. Although there are various subtypes of cybercrime, they can all be categorized into two larger types – crimes that target individual computers or networks and those that target the device owners.
Some of the most common types of cybercrime include bank information theft, identity theft, cyberterrorism, online predatory crimes, and online stalking. Not all cybercrimes are end-game actions. Some of them are simply one small step in a much larger scheme that extends to the offline world as well.
What is a DDoS Attack?
A DDoS attack is most often carried out by a botnet or zombie army of computers. It stands for distributed denial-of-service attack. The terminology refers to the disruption of services – either of a network or, say, a website. This is achieved by flooding target devices with unwanted internet traffic that hampers their performance.
The most common targets for DDoS attacks are online vendors, marketplaces, as well as other businesses that depend on having a stable connection and cannot afford to lose bandwidth. DDoS attacks may not only slow the performance of the targeted system but can also corrupt data or lead to data loss, not to mention significant financial losses.
What is Identity Theft?
Identity theft is used to describe any unauthorized gathering of personal identifying information, achieved by any means, physically or in the virtual world. Identity theft can be done via shoulder-surfing, stealing bank statements, obtaining fingerprints, dumpster diving, and so many more methods. The perpetrator uses this information to assume the victim's identity and gain personal benefit.
In this day and age, identity theft is more often than not classified as a cybercrime due to the fact that it involves hacking computer networks and databases for private information. It can also be done via spyware, keyloggers, planting viruses, email phishing, and other types of actions classified as cybercrimes.
What is a Keylogger?
There are two types of keyloggers. There are hardware keyloggers and software keyloggers. Regardless of which one is used, the main goal is always the same: tracking someone's keystrokes in order to monitor and record whatever it is they're doing on a device, whether they're browsing the internet, writing emails, writing code, etc.
Keyloggers are not always used with malicious intent. They can be used in cognitive writing research, to monitor employees on their work computers, or monitor underage kids and their online activities. However, they tend to have a negative connotation since they're most often used as standalone tools or part of advanced rootkits to steal confidential information or grant access to target devices.
What is Malware?
The term malware (short for malicious software) denotes all harmful pieces software such as computer viruses and worms, Trojans, ransomware, and adware, among others. Cybercriminals use it to establish a backdoor into foreign systems, create botnets, and launch various attacks for the purpose of stealing, corrupting, or deleting data on the target systems.
A malware suite, or a collection of more than one types of malicious software, is often referred to as a rootkit. Multiple types of covert malware programs can be embedded in a single application or file.
What is Phishing?
Phishing is a fraudulent act that involves the theft of credit card numbers, usernames, passwords, and other sensitive information in which a criminal poses as a trustworthy individual or business. Over the internet, phishing usually involves the use of fake websites with seemingly trustworthy domain names.
Although quite dangerous, phishing is usually easily avoidable if the user exercises more caution when opening attachments, disclosing their personal information, checking website URLs, and using up-to-date antivirus software. Phishing can't be successful without some involuntary help from the victims themselves, hence the need for cybercriminals to impersonate legitimate entities when phishing for information.
What is Ransomware?
Ransomware is a type of malware that is most often associated with holding certain files, data, or financial assets hostage. This malware can be remotely installed via a backdoor or downloaded by the user from infected websites or attachments. Once inside the target's system, the malware encrypts information that cannot be decrypted without a key. Other designations for ransomware include crypto-Trojan, crypto-worm, or crypto-virus.
Ransomware is also sometimes used to steal information. As a result, it is used in online blackmailing schemes in which the victim is threatened with the release of potentially compromising personal information that's been encrypted by the hacker unless a ransom is paid off. Finding the source of the attack or the attacker is generally very difficult since most ransoms involve cryptocurrency payouts.
What is a Rootkit?
Rootkits are usually, but not always, malware suites comprised of multiple programs and viruses designed to grant access to a computer or computer network by secretly exploiting various system vulnerabilities. Rootkits can be distributed via attachments, adware, email links, and other means.
The most common goal for a rootkit is establishing a backdoor access to the target system, which will allow the attacker to easily steal information, documents, money, or passwords. The perpetrator can also use this to wreak havoc on the system by corrupting data, disrupting traffic, deleting data, or slowing down the system's performance. Modern antivirus programs have rootkit detection, whereas this was a much more difficult problem to deal with in the past.
What is a Scam?
Best Antivirus For Mac Os X El Capitan
A scam is a fraudulent and criminal action initiated by an individual or group of individuals for the purpose of extracting sensitive information, stealing money, repurposing goods, etc. Internet scams include fake donations, cold calls, chain mail, online surveys, and many more.
A large majority of scams are done via the internet due to the ease of access that scammers have to networks of people. Some scams are quick schemes with a well-defined goal while others are larger cons that involve multiple steps in establishing trust, obtaining sensitive information, and stealing money.
What is Social Engineering?
In the context of computer security, social engineering involves the use of psychological manipulation of individuals and groups using various techniques. Regardless of the specific technique that is used, social engineering is often employed with malicious intent and for the purpose of stealing confidential information or disrupting the normal operation of certain organizations.
Phishing is one aspect of social engineering as it involves tricking the target into revealing sensitive information. However, social engineering involves both low-tech and high-tech methods of manipulating victims. Just like with phishing, the perpetrator aims to earn the victim's trust in order to gain access to information they can use to either harm the target or gain something for themselves.
What is Spam?
Sending spam (also known as spamming) is the action of sending multiple unsolicited electronic messages. Spam almost always has a negative connotation but isn't always part of some illegal scheme. Spam email, for example, can simply be part of an aggressive advertising campaign for certain products or services.
On the other hand, spam email can also be used in phishing schemes. In that case, the emails likely contain infected attachments or links to fake versions of various legitimate websites. Their creators' goal is to collect personal information that can be used to extort money or information from the victim, gain access to restricted servers, or steal one's identity.
What is Email, IP, or DNS Spoofing?
Email spoofing is done to gain access to confidential information from an individual or groups of individuals. This type of action involves creating fake versions of legitimate websites that look good enough at first glance, to convince the target to reveal whatever information is requested.
DNS spoofing can be a standalone scam or part of an email spoofing scan. It involves diverting traffic from trusted websites to fake versions of those websites, from which the website owners can get the victims' personal identifying information, usernames and passwords, credit card information, etc.
IP spoofing is not always used with malicious intent. Some people use IP spoofing and VPN services to access georestricted websites or hide their online activities. However, it can also be used to gain access to restricted networks in order to steal information or carry out some other malicious activities.
What is Spyware?
Spyware is a subclass of malware programs that may include keyloggers, adware, Trojans, system monitors, tracking cookies, and other programs designed to monitor, record, and steal information. Most spyware programs are designed to operate covertly, without the user's knowledge or consent. They can be standalone programs, remotely installed, or programs that need to be triggered by an action on the end-user's device.
Spyware may collect a wide range of data or very specific information from targeted devices. In the case of adware, it may simply collect marketing-related information. In the case of keyloggers, however, it can steal usernames, passwords, identifying bank credentials, and so much more.
What is an SQL Injection Attack?
An SQL injection attack is any action that inserts malicious SQL code into an SQL database for the purpose of gaining access to data and modifying, corrupting, or deleting it. It can either be done for financial gain or to wreak havoc on someone's business, thus causing significant economic damage.
Antivirus Mac Free
Most SQL injection attacks are directed towards online vendors and online marketplaces. However, due to the constant attacks against the e-commerce sector, there are more than a few ways to secure and protect websites with SQL databases against these attacks. Today, very little damage can be done to protected systems, thanks to the advanced antivirus and firewall programs available for small businesses and large enterprises.
What is a Trojan Horse?
A Trojan horse, also known as a Trojan virus or simply Trojan, is a type of computer virus that can cause harm to a system once activated. Unlike a computer worm, a Trojan requires activation on the end-user's system to do its job. However, this is not a type of virus that self-replicates and spreads to other systems.
Most of the time, a Trojan virus is used to establish backdoor access or remote access into the target system. Some Trojans are used to steal information directly or to download other malicious software onto the target computer or network.
What is a Zero-Day Exploit?
Best Antivirus For Macos 2020
A zero-day exploit, sometimes called a zero-hour exploit is not one particular exploit but rather a category of computer exploits. It includes all unknown or recently discovered computer exploits. Any exploit that's known only to the attacker and is used to take advantage of a vulnerability is called a zero-day exploit.
These exploits are virtually impossible to defend against, because they are inconspicuous and work thanks to undiscovered or unpublicized vulnerabilities in various apps or networks. Once such an exploit has been made public, it is called an N-day exploit, with N being the number of days since the exploit was first discovered and since developers have started working on fixing it.
Trustpilot / Airo
Trustpilot / Avast
Trustpilot / BitDefender
Trustpilot / BullGuard
Trustpilot / Intego
Trustpilot / Kaspersky
Trustpilot / McAfee
Trustpilot / Norton
Trustpilot / Panda Security
Trustpilot / Total AV
AV-Test / Windows
AV-Test / Mac
AV-Test / Mobile
SoftwareLab.org is an independent software testing company. To keep our information free for you to access, we may earn a referral commission when you make a purchase using one of the links on our site. In doing so, you are supporting independent testing, for which we are grateful. Thank you.
